Packet Hacking with PowerShell - AKA Mass Defcon Pwnage
Every year, two of the biggest hacking / security conferences take place in Las Vegas: Black Hat, and DefCon.
Both are great experiences, and both have a common theme – hackers (“Intelligent folks that like to make machines do things they weren’t originally designed for”) getting together to educate each other and have fun.
Unsurprisingly, one of the places that people get together to have fun is the free open WiFi.
Aside: Open WiFi led to the nerdiest “social networking” experience I’ve ever had. I was monitoring my hotel network to see how much malicious activity was on it. One of the prominent protocols in a network is LLMNR: a name resolution protocol that queries the local subnet for computers before trying other name resolution protocols. I saw one computer making requests for another laptop (presumably to reconnect a shared drive) – looking for a machine called “johnsmithlaptop”. It was also making LLMNR requests for a couple of servers on the Microsoft internal network. I figured that this was probably John Smith that works in security at Microsoft – who I’d been meaning to catch up with anyways. I sent him a mail asking if he was at BlackHat at my hotel – he was, and we got together for drinks :)
At DefCon, they had two networks: a secure network where you downloaded user certificates and that was monitored for threats very heavily, and another. From the FAQ:
Is there a free network at DEF CON?
Why yes, DEF CON 21 is FULLY network-enabled. Now that we’ve perfected the art of a stable hacker con network, we’re ascending to a higher level - we’re providing you a network that you feel SAFE in using! Since DEF CON 18 we’re WPA2 encrypted over-the-air, with a direct trunk out to the Internet. No peer-to-peer, no sniffing, just straight to the net (and internal servers). We’ll provide login credentials at Registration. We know the 3G airwaves will be saturated so we’re putting our own cred on the line to give you a net that even we would put our own mobile phones on.
If you’re feeling frisky, we’ll still have the traditional “open” network for you - bring your laptop (we’d recommend a clean OS, fully patched–you know the procedure) because we don’t police what happens on that net. Share & enjoy!
So the free open WiFi is pretty frisky. People are constantly monitoring it with their packet analyzer of choice, looking for fun things to do.
In packet analyzers, most protocols have “wizards” coded that will parse the protocol and give you a high-level summary of what that packet was attempting to do. Here’s an example of NTP (Network Time Protocol) traffic being dissected by WireShark:
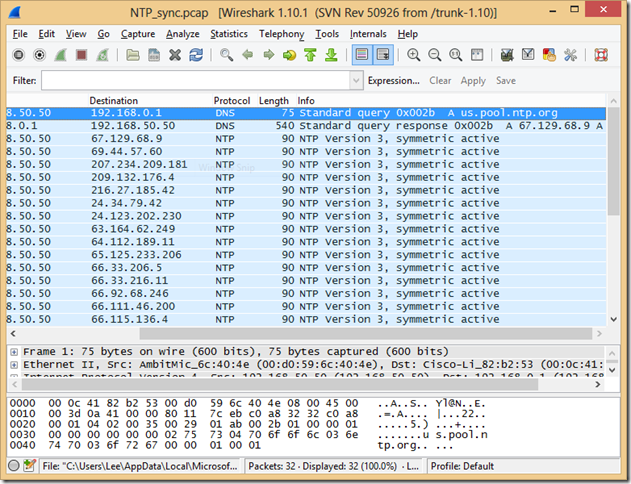
Most of the details in the “Info” column are extremely constrained – for example, describing protocol options, or maybe an IP or DNS address. However, I found one protocol during a Google Hangout I was having that supported almost arbitrary text in the “Info”, and decided to have fun. The protocol was STUN – a protocol designed to help applications figure out all of the complicated NAT translation being done to a client.
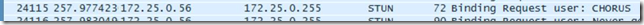
If you were monitoring the DefCon network at all you might have seen a packet like this fly by:
If you put a filter on the STUN protocol, the full beauty of the packet hacking would be exposed:
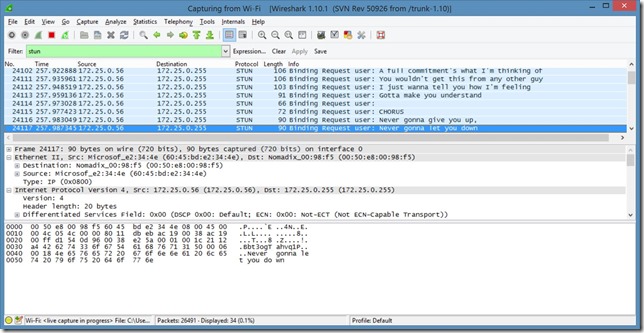
So, that’s how you (Rick) roll on the free network at DefCon.
In the next post, I’ll go through the code that made the magic happen.
