Discovering Registry Settings - PowerShell and Process Monitor
To give a glimpse into the writing process behind my upcoming “Windows PowerShell - The Definitive Guide” (O’Reilly,) I’ll occasionally post entries “as the author sees it.” This entry illustrates how to discover registry settings for programs that do not otherwise support scripted automation.
Discover Registry Settings for Programs
Problem
You want to automate the configuration of a program, but that program does not document its registry configuration settings.
Solution
Use Sysinternals' Process Monitor to observe registry access by that program. Process Monitor is available from https://docs.microsoft.com/en-us/sysinternals/downloads/procmon.
Discussion
In an ideal world, all programs would fully support command-line administration and configuration through PowerShell cmdlets. Many programs do not, however, so the solution is to look through their documentation in the hope that they list the registry keys and properties that control their settings. While many programs document their registry configuration settings, many still do not.
Although these programs may not document their registry settings, you can usually observe their registry access activity to determine the registry paths they use. To illustrate this, we will use the Sysinternals' Process Monitor to discover PowerShell’s execution policy configuration keys. Although PowerShell documents these keys and makes its automated configuration a breeze, it illustrates the general technique.
Launch and configure Process Monitor
Once you’ve downloaded Process Monitor, the first step is to filter its output to include only the program you are interested in. By default, Process Monitor logs almost all registry and file activity on the system.
First, launch Process Monitor, then press Ctrl-E (or click the magnifying glass icon) to temporarily prevent it from capturing any data. Next, press Ctrl-X (or click the white sheet with an eraser icon) to clear the extra information that it captured automatically. Finally, drag the target icon and drop it on top of the application in question. You can press Ctrl-L (or click the funnel icon) to see the filter that Process Monitor now applies to its output.
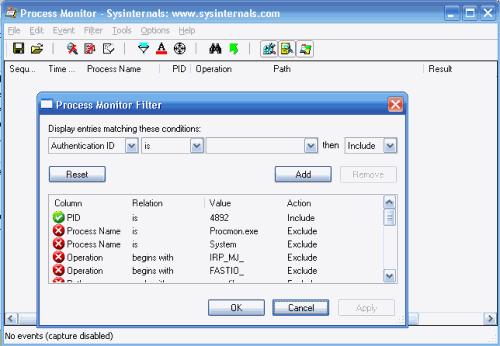
Figure 18-2. Process Monitor ready to capture
Prepare to manually set the configuration option
Next, prepare to manually set the program’s configuration option. Usually, this means typing and clicking all of the property settings, but just not pressing OK or Apply. For this PowerShell example, type the Set-ExecutionPolicy command line, but do not press Enter.
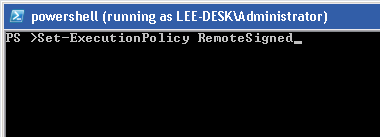
Figure 18-3. Preparing to apply the configuration option
Tell Process Monitor to begin capturing information
Switch to the Process Monitor window, then press Ctrl-E (or click the magnifying glass icon.) Process Monitor now captures all registry access for the program in question.
Manually set the configuration option
Press OK, Apply, or whatever action it takes to actually complete the program’s configuration. For the PowerShell example, this means pressing Enter.
Tell Process Monitor to stop capturing information
Switch again to the Process Monitor window, then press Ctrl-E (or click the magnifying glass icon.) Process Monitor now no longer captures the application’s activity.
Review the capture logs for registry modification
The Process Monitor window now shows all registry keys that the application interacted with when it applied its configuration setting.
Press Ctrl-F (or click the binoculars icon), then search for RegSetValue. Process Monitor highlights the first modification to a registry key.
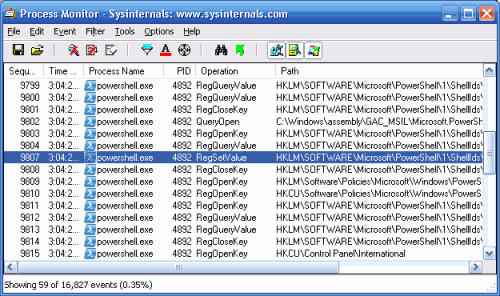
Figure 18-4. Process Monitor’s registry access detail
Press Enter (or double-click the highlighted row) to see the details about this specific registry modification. In this example, we can see that PowerShell changed the value of the ExecutionPolicy property (under HKLM:\Software\Microsoft\PowerShell\1\ShellIds\Microsoft.PowerShell) to RemoteSigned. Press F3 to see the next entry that corresponds to a registry modification.
Automate these registry writes
Now that you know all registry writes that the application performed when it updated its settings, judgment and experimentation will help you determine which modifications actually represent this setting. Since PowerShell only performed one registry write (to a key that very obviously represents the execution policy,) the choice is pretty clear in this example.
Once you’ve discovered the registry keys, properties, and values that the application uses to store its configuration data, you can use the techniques discussed in @TODO Ref Modify or delete a registry key value to automate these configuration settings. For example:
PS >$key = “HKLM:\Software\Microsoft\PowerShell\1\” +
>> “ShellIds\Microsoft.PowerShell”
>>
PS >Set-ItemProperty $key ExecutionPolicy AllSigned
PS >Get-ExecutionPolicy
AllSigned
PS >Set-ItemProperty $key ExecutionPolicy RemoteSigned
PS >Get-ExecutionPolicy
RemoteSigned
