Maslow's Hierarchy of Security Controls
You’ve probably heard of Maslow’s Hierarchy of Needs. It’s a useful way to think about human needs and the priority in which we tend to fulfill them. Somebody dealing with a physiological crisis such as lack of food and water is unlikely to improve their situation much by focusing on self-actualization issues like finding opportunities for their artistic expression. When thinking about an organization’s security stance or security controls, I find that there is a very close parallel to Maslow’s Hierarchy of Needs. I call it Maslow’s Hierarchy of Security Controls. If an organization is struggling to contain known viruses exploiting patched vulnerabilities, they are unlikely to improve their situation much by trying to address zero-day attacks that operate in a “forensically clean” stealth mode.
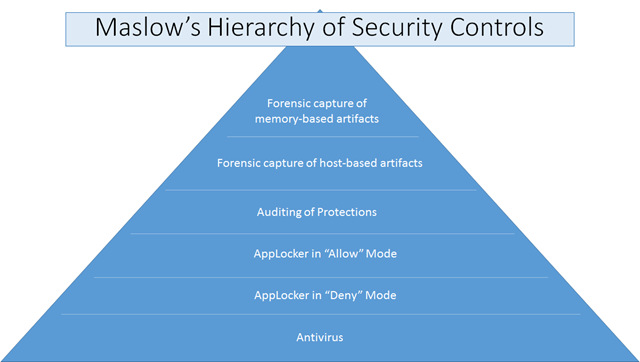
When it comes to system defenses and security controls, there are many controls and mitigations you can employ:
- Antivirus
- AppLocker in “Deny” Mode (or another technology that does Application Blacklisting)
- AppLocker in “Allow” Mode (or another technology that does Application Whitelisting)
- Auditing (especially of implemented security controls)
- Forensic capture and analysis of host-based artifacts (filesystem, network, registry, etc.)
- Forensic capture and analysis of memory-only artifacts
Each control depends on the protection of those below it in the hierarchy of security controls. If you only add security controls near the top of the hierarchy, attacks can trivially avoid those controls by exploiting weaknesses lower in the hierarchy. Here’s a deeper look at these controls, and how they build on each other:
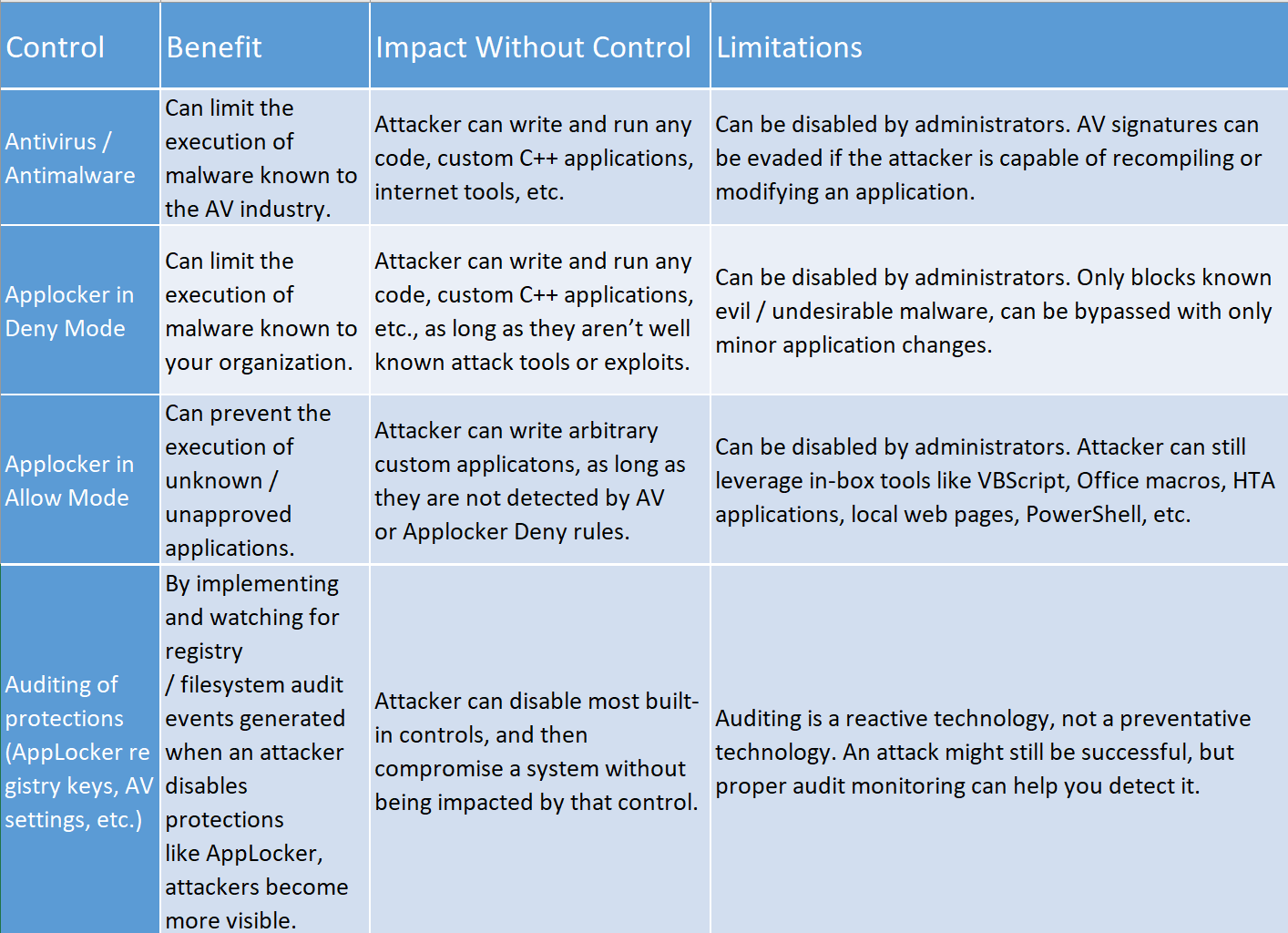
So if you find yourself or an organization considering mitigations or security controls at a high level in Maslow’s Hierarchy of Security Controls, be sure that you’ve covered your bases at the lower levels, too. Otherwise, your return on investment will be exceedingly low. (Link to this in PPTX format: Maslow’s Hierarchy of Security Controls)
